
Sigma Male 20 Personality Traits to Identify Him in 2022 Sigma male
sigma master 24 branches 37 tags Code nasbench Merge PR #4659 from @nasbench - Reduce `Remote PowerShell Session (PS… 36290c5 4 days ago 15,992 commits .github chore: archive new rule references and update cache file ( #4652) last week deprecated Merge PR #4577 from @nasbench - Multiple Fixes & Updates 2 weeks ago documentation
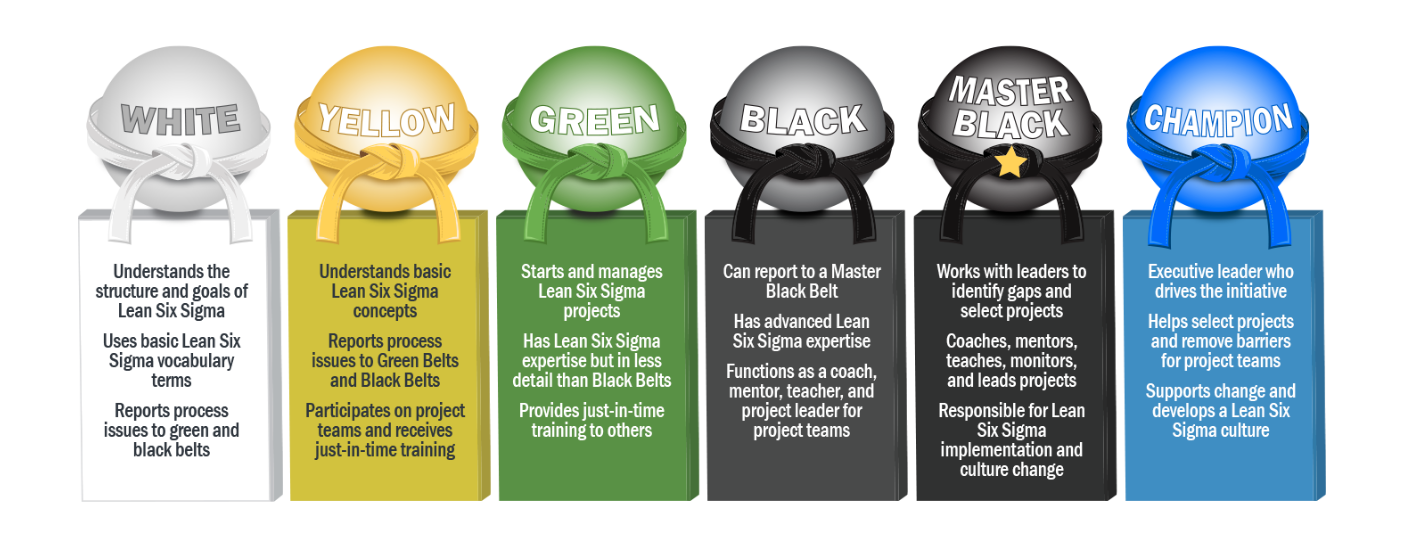
What Is Six Sigma?
SOC Prime users are now armed with high-quality detection content to proactively defend against the most common adversary behaviors and tools applied by threat actors in destructive cyber-attacks. The Sigma Rules list called "Smoking Guns" is based on the recommendation engine that harnesses collective industry expertise and peer-driven.

mexicoukraine Blog
Kaspersky actively involves SIGMA in its practice: the latest report on crimeware, " The common TTPs of modern ransomware groups ", includes over 70 SIGMA rules that simplify the work of security specialists. During this webinar, Kaspersky experts will provide a short overview of the SIGMA history, explain the main technical details - and.

60+ best sigma male quotes and captions for your photos Tuko.co.ke
List of open source community Sigma rules that match the sysmon events recorded via execution of the file under scrutiny in a sandbox. Number of matching Sigma rules of all the different severities. Number of matching Sigma rules of this specific severity. Sigma rule name. Sigma rule description. View the Sigma rule.
Sigma Rules List PDF Download 2023
May 16, 2022 · 14 min read The Case for SIGMA Rules Creating SIGMA Rules Recommended Background & Context Let's Create a Simple SIGMA Rule! An idea (and some thoughts on detection engineering with SIGMA) A data source / A log source Fitting the detection idea to SIGMA Logsource component Detection component Selection sub component (s):

11 Personality Traits Of A Sigma Male That Sets Them Apart (2023)
What Is Sigma Rule? A Sigma rule is an open-source, generic signature format used in cybersecurity, specifically for the creation and sharing of detection methods across Security Information and Event Management (SIEM) systems. Sigma rules translate and standardize threat-detection practices, making them accessible and reusable regardless of.

Sigma Rule Attitude Whatsapp Status Video, Best Attitude HD Status Video
Sigma rule for NotPetya Ransomware Activity detection was developed and shared with the community by Florian Roth and Tom Ueltschi. Simultaneously, the SOC Prime Team helped the victims of the NotPetya attack on-site and remotely using Sigma rules alongside its own SIEM-native content..

8+ Sigma Omegaverse RohitEleanore
Sigma Rules Examples 0xffccdd · Follow 3 min read · Dec 2, 2022 Sigma rules are a powerful tool for enhancing the capabilities of SIEM (Security Information and Event Management) systems.

15 Signs You’re An Alpha Male
Gamma Male Omega Male Zeta Male But there is one type of male that lives outside the hierarchy. He's not subject to the alpha's dominance, nor does he want to compete with the betas - he is the Sigma Male. Sigma males have a set of characteristics that make them both high-value and immune from social pressures.

Pin on Lifestyle
Sigma Rules are YAML-written textual signatures designed to identify suspicious activity potentially related to cyber threats anomalies in log events. One of the main advantages of these rules is their standardized format that permits writing the rule once and applying it across various SIEM products without needing to rewrite the rule.

Alpha Male Characteristics, Alpha Male Traits, Male Mindset, Male Logo
The Smoking Guns Sigma Rules list serves as a universal solution for a wide cybersecurity audience offering high-fidelity alerts to identify critical security gaps and providing an immense.
Sigma Rule Memes And Meme Sound Download Memes.co.in
Sigma rules are YAML files that contain all the information required to detect odd, bad or malicious behaviour when inspecting log files - usually within the context of a SIEM.

Importing Sigma Rules to Azure Sentinel Microsoft Tech Community
The YAML Structure Sigma Rules are structured in a YAML format. The Sigma Rule specification documents and describes the available attributes and the values they support. As I go through this tutorial, I recommend having some example rules open to cross-reference this theory to real world implementations.

The Lone Wolf Who Is He? The Sigma Male Personality Traits You Need To
Threat Hunting Sigma rules can be used to hunt for threats: Use the rules to detect when a certain attack or threat targets your organization. Check if your organization was breached by applying Sigma rules to old logs (assuming your organization aggregates logs for at least a few months).

[PDF] Sigma Rules List PDF Download PDFfile
Sigma Rules List; Sigma rules; Crowdsourced YARA Rules; Get Started; Searching; Sigma Rules List Powered by Zendesk.
Understand Sigma Male; Characteristics, Traits, And Rules
Article Last Updated on Tue June 21, 2022 A deep dive into Sigma rules and how to write your own threat detection rules Written by Hardik Manocha Co-founder @ FourCore Sigma as a Detection Language In our previous blog post, we covered how Windows Event Log IDs can be utilized for threat hunting, featuring Sigma rules.